Digital identity is undergoing a radical transformation. As we move deeper into the digital age, our online identities are becoming as important as our physical ones. This comprehensive guide explores the cutting-edge developments shaping digital identity, from blockchain solutions to AI-powered verification, and examines how these changes will impact businesses and consumers alike.
A. The Current State of Digital Identity
-
Traditional Identity Systems
-
Reliance on usernames and passwords
-
Centralized databases vulnerable to breaches
-
Growing identity theft concerns
-
Emerging Challenges
-
Increasing sophistication of cyber attacks
-
Demand for seamless user experiences
-
Regulatory pressures (GDPR, CCPA)
-
Market Growth Projections
-
Global digital identity solutions market expected to reach $49.5 billion by 2026
-
Compound annual growth rate of 17.3%
B. Key Technologies Shaping Digital Identity
-
Blockchain-Based Solutions
-
Decentralized identity management
-
Self-sovereign identity (SSI) models
-
Case study: Microsoft’s ION network
-
Biometric Authentication
-
Facial recognition advancements
-
Behavioral biometrics (typing patterns, mouse movements)
-
Multi-modal biometric systems
-
Artificial Intelligence Applications
-
Fraud detection algorithms
-
Continuous authentication systems
-
Risk-based authentication

C. Future Trends in Digital Identity
-
Passwordless Authentication
-
FIDO2 standards adoption
-
WebAuthn implementation examples
-
Enterprise deployment case studies
-
Digital Identity Wallets
-
Government-backed initiatives (EU Digital Identity Wallet)
-
Private sector solutions (Apple Wallet integrations)
-
Cross-border interoperability challenges
-
Decentralized Identity Networks
-
DID (Decentralized Identifiers) standards
-
Verifiable credentials ecosystem
-
Industry consortium developments
D. Industry-Specific Impacts
-
Financial Services
-
KYC process transformation
-
Open banking implications
-
Fraud prevention advancements
-
Healthcare
-
Patient identity matching solutions
-
Telemedicine authentication needs
-
HIPAA-compliant identity verification
-
E-Commerce
-
Frictionless checkout experiences
-
Age verification solutions
-
Loyalty program integrations
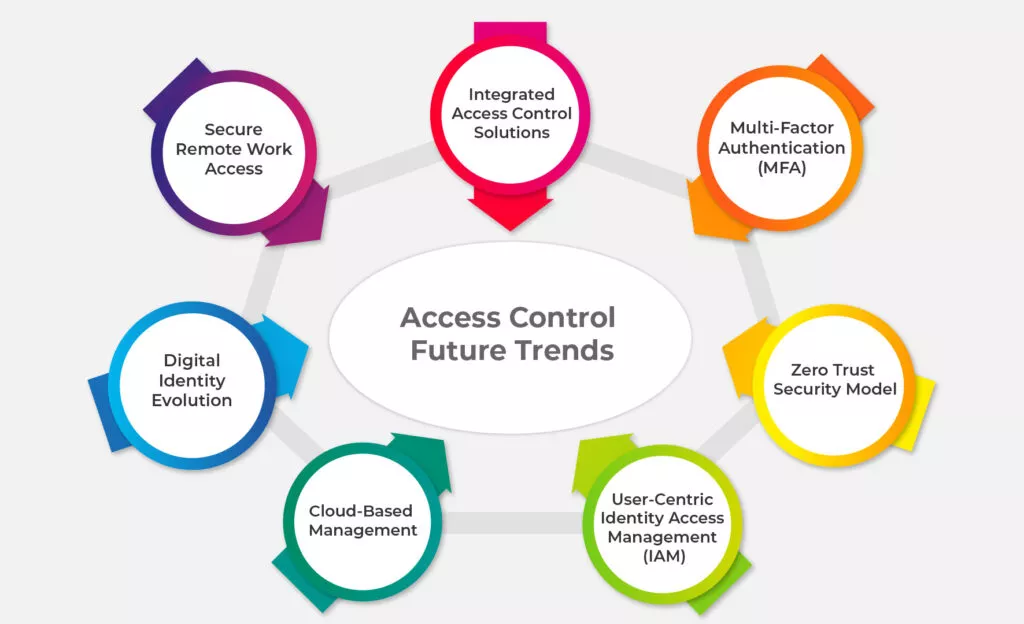
E. Security Considerations & Challenges
-
Privacy Protection
-
Zero-knowledge proof applications
-
Differential privacy techniques
-
Data minimization strategies
-
Regulatory Compliance
-
Global standards harmonization
-
Right to be forgotten implementations
-
Audit trail requirements
-
Implementation Barriers
-
Legacy system integration
-
User adoption hurdles
-
Cost-benefit analysis
F. Business Opportunities
-
New Revenue Streams
-
Identity-as-a-Service models
-
Verification API marketplaces
-
Trust scoring services
-
Operational Efficiencies
-
Automated onboarding processes
-
Reduced fraud-related losses
-
Improved customer experiences
-
Strategic Partnerships
-
Tech provider collaborations
-
Industry alliance formations
-
Government cooperation models

G. Consumer Benefits & Concerns
-
User Experience Improvements
-
Single sign-on convenience
-
Reduced authentication friction
-
Personalized services
-
Privacy Enhancements
-
Selective disclosure capabilities
-
Data ownership control
-
Transparency benefits
-
Adoption Barriers
-
Technology literacy requirements
-
Trust establishment challenges
-
Behavioral change resistance
H. Implementation Roadmap
-
Assessment Phase
-
Current identity infrastructure audit
-
Risk profile evaluation
-
Compliance requirements analysis
-
Solution Selection
-
Vendor evaluation criteria
-
Pilot program design
-
Scalability considerations
-
Deployment Strategy
-
Phased rollout planning
-
Change management approaches
-
Performance monitoring metrics
I. Future Predictions (2025-2030)
-
Mainstream Adoption Timeline
-
Enterprise adoption curves
-
Consumer acceptance rates
-
Regulatory milestone projections
-
Technology Convergence
-
IoT device identity management
-
Metaverse identity solutions
-
Quantum computing impacts
-
Societal Implications
-
Digital inclusion considerations
-
Identity sovereignty movements
-
Global trust framework developments
J. Frequently Asked Questions
-
How secure are biometric authentication methods?
Modern biometric systems incorporate liveness detection and anti-spoofing measures, making them significantly more secure than traditional passwords when properly implemented. -
What happens if my digital identity gets compromised?
Next-gen systems feature robust recovery protocols including multi-factor verification and decentralized backup mechanisms to restore identity securely. -
Will digital identity solutions work across different countries?
International standards bodies are working on interoperability frameworks, though full global compatibility remains a work in progress.
Conclusion
The future of digital identity promises unprecedented security, convenience, and user control. As technologies mature and standards coalesce, we’re moving toward an ecosystem where individuals truly own and manage their digital selves. Businesses that embrace these innovations early will gain competitive advantages in customer trust, operational efficiency, and fraud prevention.
Tags: digital identity, identity verification, biometric authentication, decentralized identity, passwordless security, identity management, cybersecurity, blockchain identity, future technology, digital transformation